If you use WP File Manager, your site might be at risk. It’s reported that hackers are exploiting a critical zero-day security vulnerability that allows them to upload files and execute malicious scripts remotely on websites running File Manager. But don’t panic, here we’ll show you how to fix the WP File Manager security flaw.
How bad is the File Manager security issue?
According to the reports, hackers were exploiting a remote code execution (RCE) flaw, that allowed them to upload malicious files and execute commands on thousands of websites using WP File Manager.
The attackers would use the exploit to upload files that contain web shells hidden in images. From there, they can run commands in the directory where WP File Manager is located (plugins/wp-file-manager/lib/files/). Another security firm reported that hackers were injecting code into the WordPress /wp-admin/admin-ajax.php and /wp-includes/user.php scripts. Hackers used six different IP addresses and the files they uploaded to vulnerable websites had names like hardfork.php, hardfind.php, or x.php.
So what could the attackers do if they exploit the vulnerability? They could do all sorts of things from stealing private data to break the site use the site to potentially mounting more attacks on other websites.
An attacker could potentially do whatever they choose to – steal private data, destroy the site or use the website to mount further attacks on other sites or the infrastructure said Ville Korhonen from Seravo.
File managers usually “contain several features that if exposed within the admin area of your WordPress installation, could cause serious problems,” says Chloe Chamberland from Wordfence. Attackers could manipulate or upload files directly from the WordPress dashboard allowing them to escalate those privileges once they’re the site’s admin area. “For example, an attacker could gain access to the admin area of the site using a compromised password, then access this plugin and upload a web shell to do further enumeration of the server and potentially escalate their attack using another exploit.” sates Chamberland.
That’s why you should uninstall utility plugins if you don’t use them often. These tools have features that allow hackers to potentially escalate their privileges if they find an exploit.
Who’s the File Manager security issue affecting?
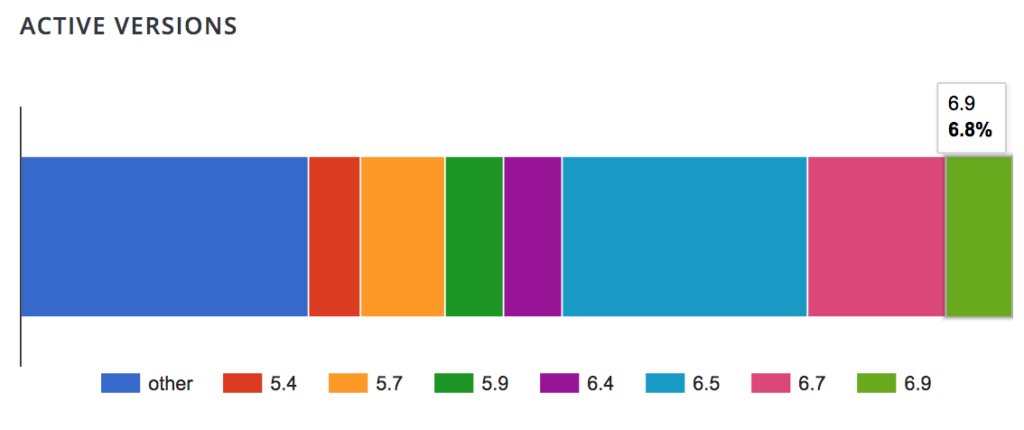
With more than 700,000 active installations, WP File Manager is one of the most popular WordPress plugins out there. This security issue affects version 6.8 and below, which nearly 93% of users have. That means that the security flaw could affect more than 650,000 sites.
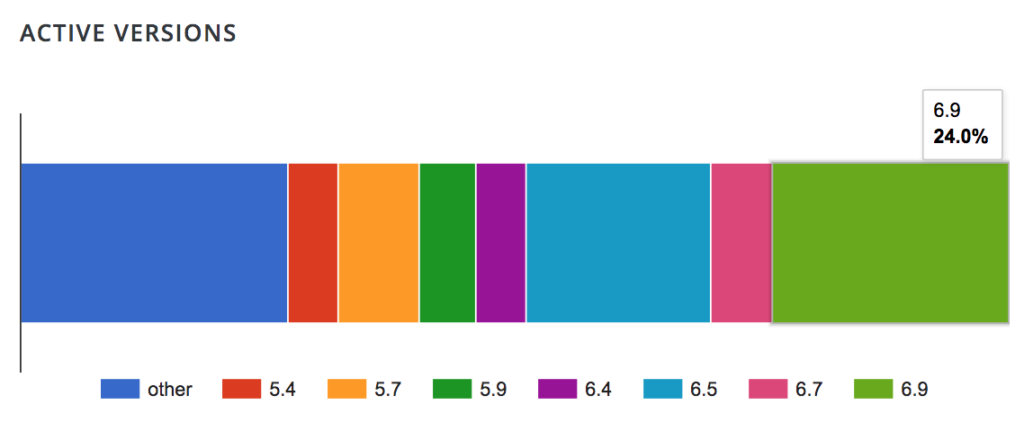
UPDATE: It’s been more than 7 days since the flaw was discovered and nearly 180,000 thousand users have downloaded the last version 6.9. However, more than 75% of File Manager’s active versions that are still exposed to this security flaw.
When was the WP File Manager security issue discovered?
The first report about unusual activity came about on September 1st.
Has this security vulnerability affected WP File Manager’s reputation?
The flaw was discovered quite recently so it’s hard to say. However, after the security vulnerability was found, many users have decided to uninstall the plugin. Since September 1st, the plugin has seen a 2.9% decrease in active install growth in the WordPress repository. We’ll see if this trend continues over time or if it’s just a temporary consequence.
How to fix the WP File Manager security flaw?
So, there are two options to fix the WP File Manager security vulnerability:
- Update the plugin to version 6.9: The team behind the plugin released a new versión 6.9 that fixes the exploit so we recommend you update to the latest version 6.9 of WP File Manager as soon as possible.
- Uninstall the plugin: Another option is to uninstall WP File Manager. Please note that you need to uninstall it, deactivating it won’t protect you against this security flaw.
So, unless you want to get rid of the plugin, you can update to version 6.9 and keep your site safe.
What should you do if you have been hacked?
Do you think you’ve been a victim of the WP File Manager exploit? Don’t panic, there’s a quick solution for you. If you think that your site has been hacked, you can reinstall WordPress to clean up the infected core files. Additionally, we recommend you change all the admin users and passwords. You can do that from the WP Dashboard > Updates. WordPress recently released a new version 5.5.1 that fixes the issues of the 5.5 update.
What can you do to keep your WordPress site safe?
There are many things you can do to keep your site safe. Some of the main recommendations to avoid the WP File Manager security flaw and other potential issues are:
- Protect the wp-admin directory
- Use strong passwords
- Do regular backups
- Update WordPress regularly
- Keep themes and plugins up to date
- Use a security plugin
- Uninstall utility plugins if you don’t use them regularly
For more ideas to improve your site security, we recommend you check out this guide.
Conclusion
All in all, the popular File Manager plugin had a security vulnerability that allowed hackers to upload files and execute commands remotely. The vulnerability affected version 6.8 and below and most websites using the plugin were among that group. However, the good news is that there are two options to fix the WP File Manager security flaw:
- Update the plugin to version 6.9
- Uninstall WP File Manager
If you think you’ve been hacked, you can reinstall WordPress and change all the admin users and passwords.
Have you been affected by this vulnerability? Did you update File Manager? Let us know in the comment section below!