If you use WPBakery as a page builder, your site might be at risk. WPBakery for WordPress has a severe vulnerability that affects more than 4 million websites. Learn what the flaw can do to your site and how to fix it.
WPBakery vulnerability
Last July, Wordfence discovered a vulnerability in the famous WPBakery page builder. The flaw allowed authenticated attackers with contributor and author level to inject malicious JavaScript code into posts and pages. On top of that, the vulnerability lets these users edit other users’ posts.
This happens because WPBakery disabled default post-HTML filtering checks in the saveAjaxFe function. So, any user with access to the page builder could potentially inject HTML and JavaScript. Additionally, WPBakery’s onclick functionality for buttons, allowed hackers to add malicious JS code in a button that would run when users click it.
As Wordfence explains:
Furthermore, contributor and author level users were able to use the
vc_raw_js,vc_raw_html, and button usingcustom_onclickshortcodes to add malicious JavaScript to posts.All of these meant that a user with contributor-level access could inject scripts in posts that would later execute once someone accessed the page or clicked a button, using various different methods.
How to fix the WPBakery vulnerability?
Even though Wordfence discovered the vulnerability more than 2 months ago and WPBakery released several updates to the plugin, these patches didn’t fully fix the flaw. However, last September 24th WPBakery launched a new version 6.4.1 that finally fixes the vulnerability.
Which WPBakery versions are affected by the vulnerability?
All the sites using WPBakery 6.4 and under are affected by this vulnerability so we highly recommend you update to the latest version 6.4.1 as soon as possible.
Additionally, make sure that all the contributor or author user-level accounts on your site are trusted.
What can you do to prevent this in the future?
Vulnerabilities in plugins aren’t new. WordPress is the most popular CMS platform so there are thousands of hackers trying to find flaws to exploit. So, to keep your site safe you can enable dual control. This is a great strategy to avoid cross-site scripting (XSS) attacks like WPBakery vulnerability. With dual control, you limit the capabilities of users with administrative capabilities. This way, instead of having one account with access to administrative and edition tasks, you can have two separate accounts: one that only has access to admin tasks and another one that can only edit and review posts.
Additionally, to avoid vulnerabilities like the one that recently affected WP File Manager, uninstall utility plugins that you don’t use.
Other recommendations to keep your WordPress site safe include protecting the wp-admin directory, doing regular backups of your files, update plugins and themes when possible, using web firewall applications and security plugins. For more information on how to keep your website safe, have a look at this guide.
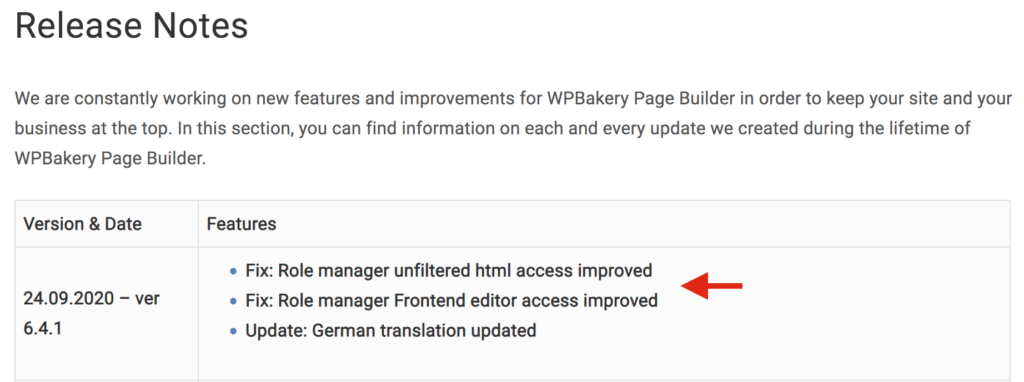
WPBakery doesn’t mention vulnerability in the changelog
Even though the WPBakery vulnerability was discovered in July and was affecting more than 4 million users, it’s curious that the page builder didn’t mention any of this in their changelog. If we have a look at the latest changelog for version 6.4.1, we see that it doesn’t mention the vulnerability at all and it doesn’t let users know that the new version fully fixes the flaw. It simply refers to the patches as improvements.
Considering how severe the vulnerability is and how it affects millions of users, one would expect a clearer message from WPBakery.
Final Words
In conclusion, WPBakery for WordPress has a vulnerability that allows users with author and contributor level to inject malicious JavaScript and HTML into posts and pages. The flaw affects all WPBakery sites using version 6.4 and under. The good news is that there’s a quick fix: update WPBakery to the latest version 6.4.1. So we recommend you update the page builder as soon as possible. On top of that, keep an eye on all contributor and author level accounts to make sure they’re trusted.
Additionally, vulnerabilities in plugins and themes aren’t new. So, it’s a good idea to follow some security best practices to keep your site safe. Finally, to prevent DDOS attacks and keep hackers at bay, check out this article.
Do you use the WPBakery page builder? Have you updated to the latest version? Let us know in the comments section below!